Information security policy
LIST OF ACRONYMS
BIM: Building Information Modeling
ENS: National Security Scheme
LOPDGDD: Law on Personal Data Protection and Guarantee of Digital Rights
POC: Person of contact (persona de contacto)
HR: Human Resources
SGI: Integrated Management System
ISMS: Information Security Management System
IS: Information Security
ICT: Information and Communication Technologies
1. PURPOSE AND SCOPE OF APPLICATION
The Executive Management of INGECID S.L. (hereinafter INGECID), within the framework of its general and non-delegable authority to determine the organization's general policies and strategies, approves this policy.
The purpose of this policy is to define and establish the principles, criteria, and improvement objectives that govern actions related to Information Security (IS) for INGECID systems that are subject to the Information Security Management System (ISMS) and within the scope of Royal Decree 311/2022, of May 3, which regulates the National Security Scheme (ENS) [1].
This policy applies to all INGECID information systems, to the people who make up its organization, and to its service providers or Information and Communication Technology (ICT) solution providers.
Therefore, this policy is limited to INGECID services and systems included in the scope of the ISMS and which cover compliance with the security requirements and measures established in the ENS [1], i.e., the information systems that support the following services:
- Design and development of civil engineering projects and technical reports.
- Training for companies in areas of civil engineering and building construction.
- Engineering in the field of nuclear energy.
- Software development for the fields of civil engineering and nuclear energy.
2. ACTIVITIES
2.1 Mission and objectives
INGECID's mission is set out in document SGI-04 Mission, Purpose, and Strategy [2], published on the organization's website (www.ingecid.es).
On the other hand, the security objectives that INGECID aims to guarantee with this policy are:
- Ensure the confidentiality, integrity, authenticity of information, and continuity in the provision of services.
- Implement security measures that enable access traceability and respect, among other things, the principle of least privilege, while also reinforcing users' duty of confidentiality with regard to the information they become aware of in the performance of their duties.
- Implement security measures based on risk.
- Train and raise awareness among INGECID members regarding information security.
- Deploy and control physical security by ensuring that information assets are located in secure areas, protected by access controls, in accordance with the risks identified.
- Establish security in communications management through the necessary procedures, ensuring that information transmitted through communications networks is adequately protected.
- Control the acquisition, development, and maintenance of information systems throughout all phases of the information systems life cycle, ensuring their security by default.
- Monitor compliance with security measures in the provision of services, maintaining control over the acquisition and incorporation of new system components.
- Manage security incidents to ensure their correct detection, containment, mitigation, and resolution, taking the necessary measures to prevent them from recurring.
- Protect personal information by adopting technical and organizational measures in response to the risks arising from processing in accordance with data protection legislation.
- Continuously monitor the safety management system, improving and correcting any inefficiencies detected.
2.2 Principles
This security policy is established in accordance with the basic security principles set out in Article 5 of the ENS [1], namely:
- Security as an integrated process
- Risk-based security management
- Prevention, detection, response, and conservation
- Existential lines of defense
- Continuous monitoring
- Periodic reassessment
- Differentiation of responsibilities
In accordance with the provisions of Article 12 of the ENS [1] and in proportion to the risks identified in each system, these principles are developed by applying the following minimum requirements:
- Organization and implementation of the security process
- Risk analysis and management
- Personnel management
- Professionalism
- Access authorization and control
- Protection of facilities
- Procurement of security products and contracting of security services
- Least privilege
- System integrity and updates
- Protection of stored and transmitted information
- Prevention against other interconnected information systems
- Activity logging and malicious code detection
- Security incidents
- Business continuity
- Continuous improvement of the security process
2.3 Regulatory framework
The main regulation affecting this policy is Royal Decree 311/2022, of May 3, which regulates the National Security Scheme (ENS) [1].
Furthermore, as part of the PC-ES-02 Context Analysis process [3], INGECID systematically records and evaluates legal and other applicable requirements. This record allows us to identify, analyze, and verify the degree of adequacy and compliance with all current legislation, including information security legislation that affects the organization.
Finally, contractual requirements arising from agreements with customers and suppliers are also expressly considered, especially those that impose specific requirements regarding information security and privacy, ensuring their integration into the company's ISMS.
2.4 Security Organization
2.4.1 ISMS Organization Chart
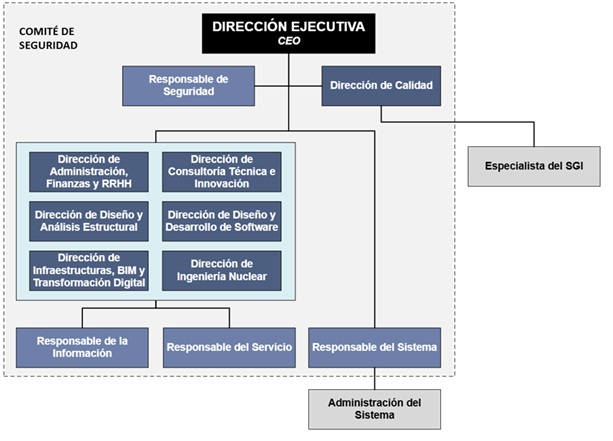
Figure 1: ISMS organizational chart
2.4.2 Coordination mechanisms
Security at INGECID is organized through the Information Security Committee, which is made up of:
- Executive Management
- Department Addresses:
- Administration, Finance, and Human Resources
- Quality
- Technical Consulting and Innovation
- Structural Design and Analysis
- Software Design and Development
- Infrastructure, BIM, and Digital Transformation
- Nuclear Engineering
- Information Manager
- Security Manager
- Head of Service
- System Manager
The person responsible for security is designated as the organization's Point of Contact (POC) for security matters.
The roles mentioned above are appointed by the Executive Management and their renewal must be approved by the Information Security Committee.
Within the execution of process PC-AP-08 Human Resources [4], the functions and responsibilities of both the Information Security Committee and each of the security roles that comprise it are defined.
This committee shall meet at least twice a year, but may meet as often as deemed appropriate. In addition, depending on the topics to be discussed, the meetings may be attended by any persons deemed appropriate by the members of this committee.
The roles and responsibilities related to the ISMS are communicated to new hires and periodically reminded to all personnel in the organization.
2.4.3 Functions and responsibilities
2.4.3.1 Information Security Committee
- Communicate and comply with this policy and associated procedures.
- Define the context of the organization and possible changes to it.
- Identify the needs and expectations of our stakeholders regarding information security, as well as their relevant requirements.
- Promote risk-based thinking and action plans to reduce risk, acting as a proactive team.
- Approve the information security risk analysis and approve acceptance of the residual risk level.
- Determine the criteria and methods necessary to ensure that both the operation and control of processes are effective.
- Identify areas for improvement or establish improvement plans when necessary, identifying changes or the inclusion of new techniques, products, procedures, or documentation in general that could improve the performance and effectiveness of the management system.
- Review documented information and contribute to its improvement.
- Analyze newly detected threats.
- Ensure that objectives, including those necessary to meet service requirements, are set at the appropriate functions and levels.
- Identify needs for awareness-raising and training activities.
- Report complaints, claims, or suggestions, and collaborate in resolving incidents, non-conformities, and corrective actions.
- Schedule and participate in audits.
- Collaborate to carry out management reviews.
- Plan new drills for the Business Continuity Plan.
- Assess the damage and determine the need to declare a disaster and activate the Recovery Plan.
2.4.3.2 ISMS roles
The duties and responsibilities of the roles of Security Manager, System Manager, Information Manager, and Service Manager are duly set out in their corresponding role descriptions. These descriptions are defined and approved by the Executive Management within the framework of the PC-AP-08 Human Resources process [4], which also includes the appointment (assignment of roles) of the corresponding individuals.
2.4.4 Conflict resolution
In the event of a conflict between the different managers who make up the organizational structure of this policy, it will be resolved by the Executive Management, and the highest requirements derived from the protection of personal data will prevail.
2.5 System security documentation
Documented information related to ENS compliance [1] is organized, coded, and approved in accordance with the general requirements established in the INGECID management system, within the framework of the PC-AP-09 Knowledge Management process [5].
All documentation related to the various management systems, specifically including that relating to the ENS [1], is centralized and stored in INGECID's corporate information systems, ensuring its accessibility, integrity, traceability, and version control.
2.6 Compliance obligations
2.6.1 Personnel
All INGECID personnel are required to be familiar with and comply with this Security Policy and the procedures, instructions, and other documented information of the IMS that develops it. INGECID, through the Security Committee, is responsible for providing the necessary means to ensure that the information reaches those affected.
2.6.2 Third parties
2.6.2.1 CUSTOMERS
When INGECID provides services to other entities or handles their information, they will be made aware of this policy, without prejudice to complying with data protection regulations if it acts as the data processor in the provision of the aforementioned services. Channels will be established for reporting and coordination with the respective Security Committees, as well as procedures for responding to security incidents.
2.6.2.2 PARTNERS AND SUPPLIERS
When INGECID uses third-party services or transfers information to third parties, they will be made aware of this policy and the security rules, procedures, and/or instructions pertaining to said services or information, without prejudice to compliance with other data protection obligations. This third party will be subject to the obligations established in said documentation and may develop its own operating procedures to comply with them. Specific procedures for reporting and resolving incidents are established. It will be ensured that third-party personnel are adequately aware of security matters, at least to the same level as that established in this policy.
When any aspect of the policy cannot be satisfied by a third party as required in the preceding paragraphs, the person responsible for Security shall issue a report specifying the risks involved and how to address them. This report must be approved by the persons responsible for the information and services affected before contracting begins.
These obligations shall be regulated by agreement, covenant, or contract defining the relationship with third parties.
2.7 Awareness and training
As part of the PC-AP-08 Human Resources process [4], training and awareness-raising activities are carried out for all staff with the aim of promoting an organizational culture focused on information security. These activities will include, among others, the following content:
- Information Security Policy.
- Fundamentals of information security and its application in the workplace.
- Identification and management of risks, vulnerabilities, and threats in information systems.
- Importance of complying with current legislation on data security and protection.
All INGECID staff must attend an information security training session at least once a year. In addition, ongoing awareness-raising activities will be established, with a special focus on new hires, who will receive specific training during their onboarding process.
People who perform duties related to the use, operation, or administration of ICT systems will receive specialized training to ensure the secure handling of systems, based on the needs of their position. This training will be mandatory before assuming any responsibility, whether due to a new hire, a change of position, or a reassignment of duties.
2.8 Risk management
All information systems affected by this policy, as well as all personal data processing carried out by INGECID, must be subject to a risk analysis that allows the threats and risks to which they are exposed to be identified, assessed, and managed.
This analysis will be carried out in the following cases:
- Periodically, at least once a year.
- When significant changes occur in the information managed or the services provided.
- Following the occurrence of a serious security incident or the detection of critical vulnerabilities that could compromise the confidentiality, integrity, availability, authenticity, and traceability of information.
The person responsible for security will be in charge of ensuring that risk analyses are carried out and identifying gaps and weaknesses in systems and processes. They must also report the results obtained to the Security Committee and propose any necessary corrective or improvement measures.
2.9 Personal data
INGECID will only collect personal data when it is appropriate, relevant, and strictly necessary in relation to the legitimate purposes for which it has been obtained. At all times, the necessary technical and organizational measures will be taken to ensure compliance with current regulations on personal data protection.
When an INGECID information system manages personal data, the provisions of the Law on Personal Data Protection and Guarantee of Digital Rights (LOPDGDD) [6], as well as its implementing regulations, shall apply. All of this is without prejudice to additional compliance with the requirements established in the ENS [1].
Likewise, all information systems must comply with the security levels required by data protection regulations, depending on the nature, scope, context, and purposes of the processing, as well as the risks identified for the rights and freedoms of individuals.
2.10 Review and approval
In order to ensure the validity, adequacy, and effectiveness of this document, two types of review activities are established:
- Systematic periodic reviews: carried out in a planned manner, at least once a year by the Information Security Committee.
- Unplanned inspections: carried out in response to:
- any security event or incident that could significantly increase the current level of risk or has had an impact on the security of INGECID's information.
- detection of relevant incidents
- changes in the legal or regulatory framework that may affect the validity of this policy.
Finally, if as a result of these reviews, it is necessary to modify this policy, the new policy will be approved by INGECID's Executive Management and stakeholders will be duly informed through the same channels used for its dissemination.
3. REFERENCES
[1] Royal Decree 311/2022, of May 3, regulating the National Security Scheme (ENS).
[2] INGECID, SGI-04 Mission, purpose, and strategy.
[3] INGECID, PC-ES-02 Context Analysis.
[4] INGECID, PC-AP-08 Human Resources.
[5] INGECID, PC-AP-09 Knowledge Management.
[6] Organic Law 3/2018, of December 5, on the Protection of Personal Data and Guarantee of Digital Rights (LOPDGDD).
Prepared by the Information Security Officer and approved by senior management
APPROVAL DATE: 03/10/2025
DOCUMENT: SGI-03
REVIEW: 00






